Cyber Warfare: Understand Threats, Examples, and Defensive Strategies
Cyber warfare has rapidly evolved in the digital age to become a major concern for governments, businesses, and individuals alike. This article dives deep into the realities of cyber warfare, providing clear examples, and concrete strategies to protect yourself and your organization. Discover how to defend against these evolving threats.
What is Cyber Warfare? A Definition for the Modern Age
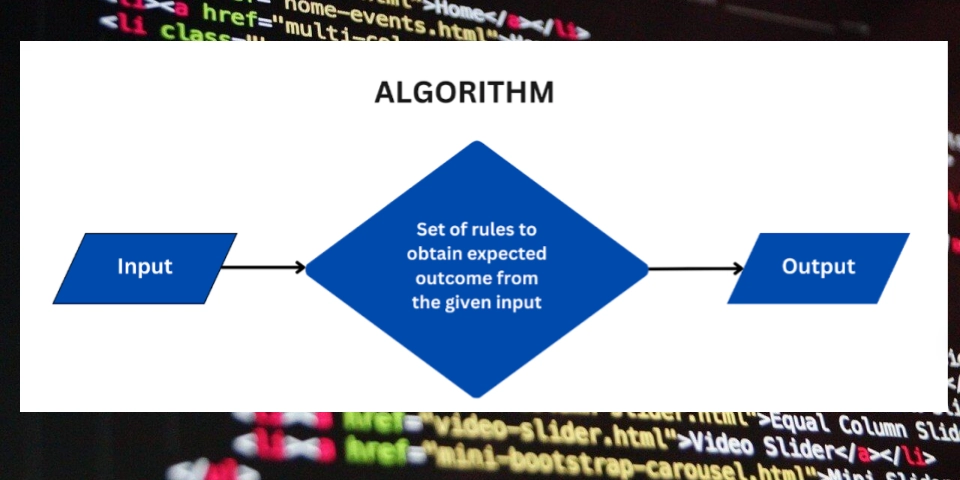
Cyber warfare involves state-sponsored or politically motivated cyberattacks intended to disrupt, collect intelligence, or sway political influence. Think digital battles fought with code instead of conventional weapons. The goal is often to destabilize a nation by targeting its economy, critical infrastructure, or public opinion from the shadows. This digital landscape is often unseen, but the damage is very real.
Unveiling the Arsenal: Different Forms of Cyber Warfare Today
The methods used in cyber warfare are constantly diversifying. Here’s a look at some common tactics:
- Economic Sabotage: Disrupting financial systems and markets.
- Espionage: Stealing sensitive data from government or defense networks.
- Grid Attacks: Targeting electrical grids and communication networks.
- Information Warfare: Spreading propaganda and misinformation.
- Denial-of-Service (DoS) Attacks: Overwhelming systems to shut them down.
- Insider Threats: Exploiting compromised employees for sabotage.
These cyber warfare tactics are designed to cripple operations, shatter trust, and gain strategic advantage without physical conflict.
Real-World Cyber Warfare Examples: Lessons from the Trenches
History is full of examples showing the damaging effects of cyber warfare. These incidents are a stark warning about the stakes involved:
- Stuxnet Worm: Crippled Iran's nuclear program, highlighting the destructive power of targeted malware.
- Fancy Bear Attacks: Russian group disrupted Ukrainian artillery systems, showing how cyberattacks impact military operations.
- North Korea vs. Sony Pictures: Revealed how cyber tactics can be used for political intimidation on a global scale.
Such instances are proof that cyber warfare has serious real-world consequences, impacting diplomacy, defense readiness, and public safety.
Defending Your Digital Kingdom: How to Mitigate Cyber Warfare Risks
Why does cyber warfare pose such a threat? The answer is complicated. Motivations range from gaining strategic advantage and revenge, to ideological supremacy and economic disruption. As threats evolve, outdated defenses just won't cut it.
Here's how to strengthen your defenses:
- Conduct regular risk and vulnerability assessments: Identify weak spots before attackers do.
- Maintain up-to-date cybersecurity tools: Stay ahead of emerging threats with the latest tech.
- Educate users and enforce strict access controls: Human error is a major vulnerability; train your people.
- Invest in threat intelligence and detection technologies: Detect and respond to attacks faster and smarter.
Platforms like CloudDefense.AI are also powerful options. They use AI-driven analysis to proactively detect and neutralize cyber threats early.
Preparing for Tomorrow's Digital Battle: Building Cyber Resilience
Cyber warfare is not some far-off threat—it's today's reality. Developing a strong, effective cybersecurity framework is absolutely vital for both governments and businesses. It is critical for national resilience and organizational continuity.